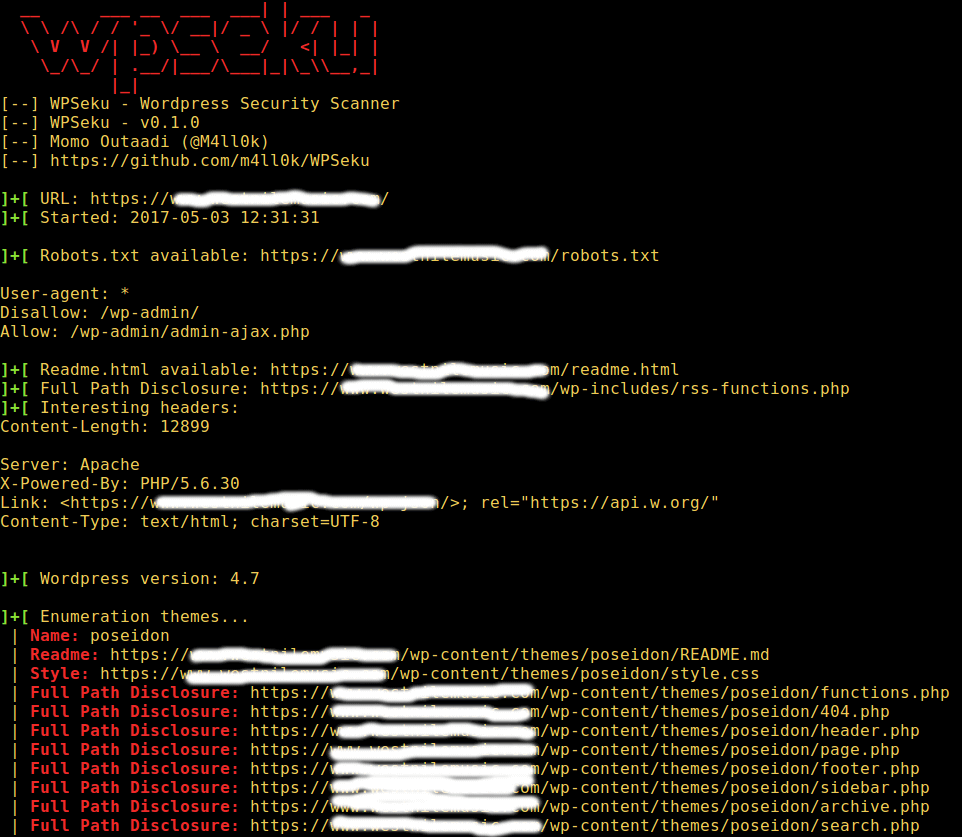
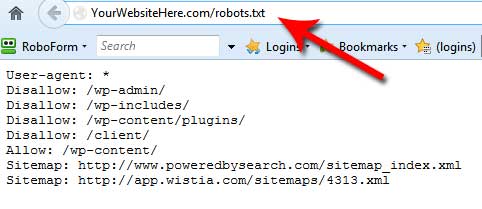
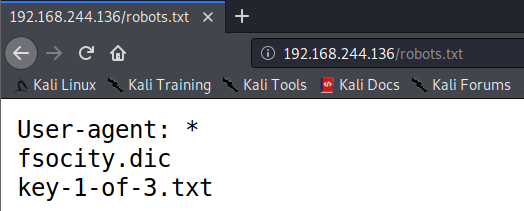
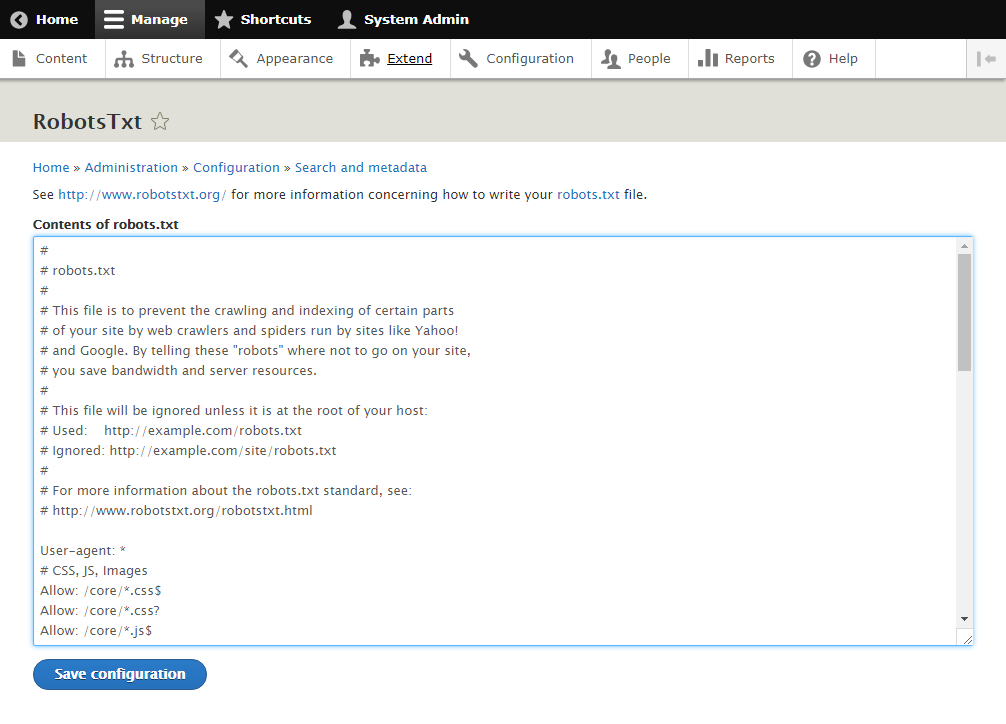
WeChat robots.txt was accidentally opened to foreign search engines. Tencent responded that the vulnerability has been fixed-Tencent WeChat QQ微信-breakinglatest.news-Breaking Latest News

Sophos on Twitter: "The concept of begging for a reward for innocuous or meaningless reports (aka "beg bounty") appears to be reaching a fever pitch. This growth appears to be fueled by
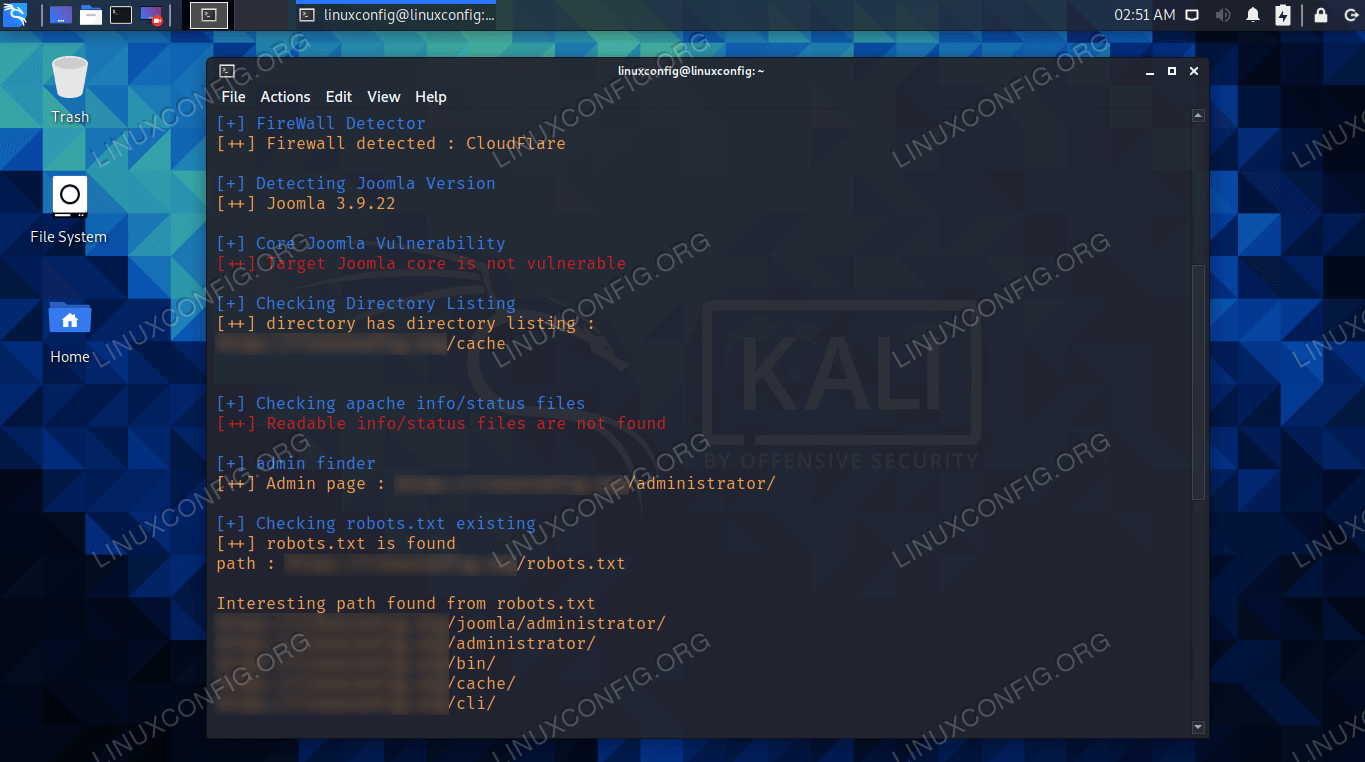
Use JoomScan to scan Joomla for vulnerabilities on Kali - Linux Tutorials - Learn Linux Configuration