Cyber Security People Process Technology Framework | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas

Best Data Security Software Process Flow For Company Online Database Security Elements PDF - PowerPoint Templates

D14.2: Study on Privacy in Business Processes by Identity Management: Future of IDentity in the Information Society



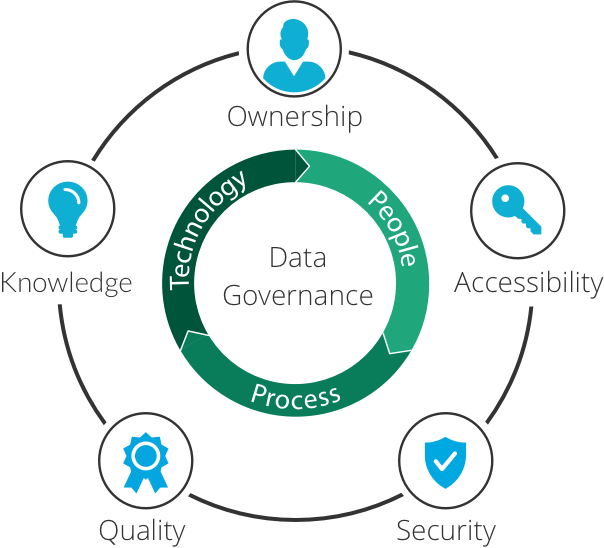



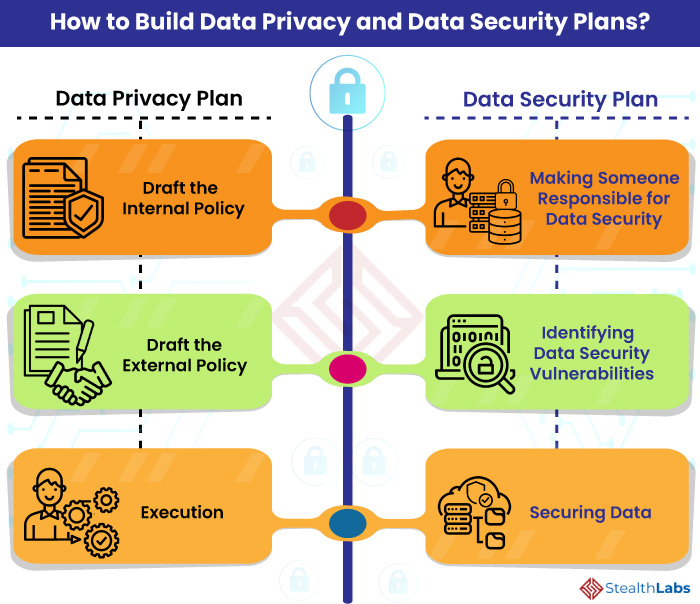
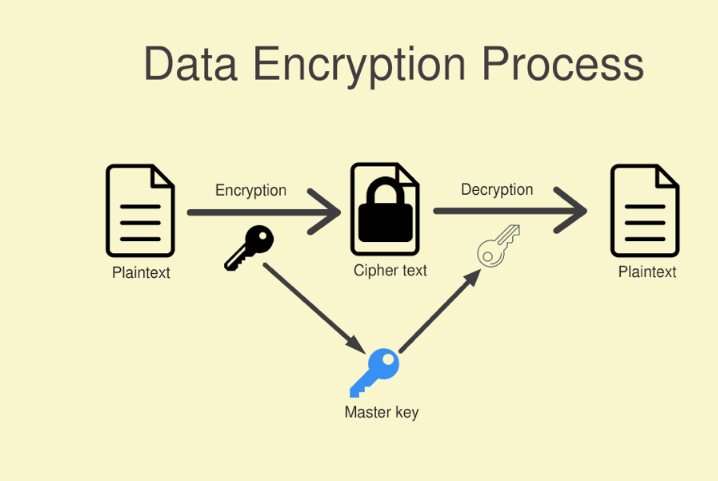







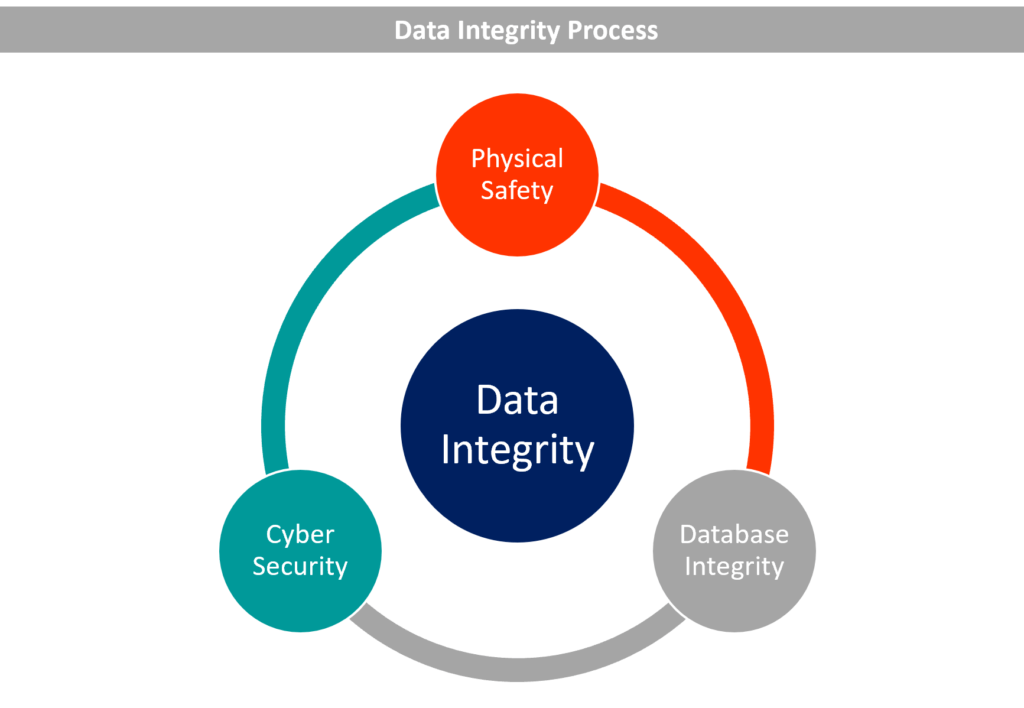
![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/05/Difference-between-data-privacy-and-data-security.png)